The aircraft safety system known as the Traffic Alert and Collision Avoidance System (TCAS) can be coerced into sending an airplane on a mid-air rollercoaster ride – much to the horror of those onboard.
Researchers were able to cobble together an effective method for spoofing the TCAS using a $10 USB-based Digital Video Broadcasting dongle and a rogue transponder, for communicating with aircraft.
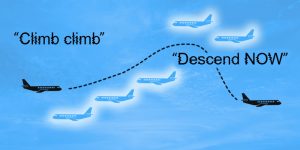
“We have shown that careful placing of fake aircraft through rogue transponder broadcasts can cause an aircraft under autopilot control to climb or descend towards legitimate traffic,” wrote Pen Test Partners’ Ken Munro in a blog post outlining his research.
Those “fake aircrafts” can trigger an airplane’s collision avoidance system to kick-in. That will then alert a pilot to either climb in altitude or descend to avoid a mid-air collision. In some cases, mostly on Airbus, researchers said the aircraft automatically follows what is known as the TCAS “Resolution Advisory” (autopilot) and climbs or descends with no input from the pilot.
For the record, Munro’s proof-of-concept attack was conducted on a flight simulator.

Spoofing the Traffic Alert and Collision Avoidance System is not new. At a Black Hat USA 2012 session, researcher Andrei Costin showed how attackers could exploit weaknesses in what is called the Automatic Dependent Surveillance-Broadcast (ADS-B) technology. In 2016, a group of researchers, associated with the University of Oxford, also showed how to spoof TCAS traffic (PDF).
“We’ve taken this further and investigated how airplanes equipped with autopilots capable of flying a resolution advisory themselves would respond in certain scenarios,” Munro wrote.
In an email to Threatpost he added, “We used similar techniques but were investigating the effect on autopilots. We wanted to see if we could cause the plane to climb or descend consistently in the direction we wanted… By careful placing of rogue broadcasts, we could send the airplane on a roller coaster, or potentially climb towards genuine traffic. Note that the other traffic should then climb out of the way. It all adds confusion in congested airspace.”
Munro’s research focused on Radio Frequency (RF) communications tied to an aircraft’s transponder data.
“TCAS uses responses from secondary surveillance radar transponders – there are two types used to compute the position of other aircraft. Mode S transmits a unique 24bit aircraft address along with altitude and GPS-derived position data, Mode C transmits a 4 digit transponder code and altitude information only so the TCAS unit itself calculates range and bearing based on these transmissions,” he wrote.
He added, “Data packets are sent over 1090MHz using Manchester encoded PPM at 1Mbps. The data structure is actually easy to decode and a cheap, $10, DVB USB dongle can pick them up for you to plot aircraft data yourself.”
By creating a fake “wall” of airplanes, the researcher was able to coax a targeted airplane to climb and descend.
The caveats to pulling off this type of attack are varied. For starters, if the TCAS Resolution Advisory system is turned off the hack won’t work. Secondly, the fake airplanes won’t show up on a radar the pilot might disregard the warnings.
“Further, ground controllers also have systems to identify conflicting traffic. Indeed, a ground controller will probably identify potential traffic well before TCAS would alert,” wrote the researcher. He added that it is not uncommon with light aircraft that Mode C and Mode S transponders (transmitting height data) that either may be misconfigured.
Caveats aside, Munro worries that pilots “could first be irritated in to disabling the TCAS RA, then would be less able to deal with a legitimate TCAS alert. A version of the ‘Crying Wolf’ attack.”
He added the next-generation of TCAS, known as ACAS-X, makes TCAS spoofing much harder.
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.
Also, don’t miss our latest on-demand webinar from DivvyCloud and Threatpost, A Practical Guide to Securing the Cloud in the Face of Crisis, with critical, advanced takeaways on how to avoid cloud disruption and chaos.